Security in Cloud Computing
Introduction
- Security in cloud computing is an important concern.
- Data in the cloud is necessary to be stored in encrypted form. It restricts the client from accessing the shared data directly. For this purpose proxy and brokerage services are necessary to employ.
- Encryption helps to protect transferred data as well as the data stored in the cloud. Encryption also helps to protect data from any unauthorized access, but it does not prevent data loss.
Planning of security
In security planning, before deploying a particular resource to cloud there is a need to analyze different aspects of the resources which are as follow:
- Select resource which requires to move to the cloud and examine its sensitivity risk.
- The cloud service models i.e IaaS, PaaS and SaaS are necessary to be considered for security at different level of services.
- The cloud types, i.e public, private, community, hybrid also need to be considered.
- The risk in a cloud deployment generally depends on the types of cloud and service models.
Security Boundaries
- A specific service model defines the boundary among the responsibilities of customer and service provider.
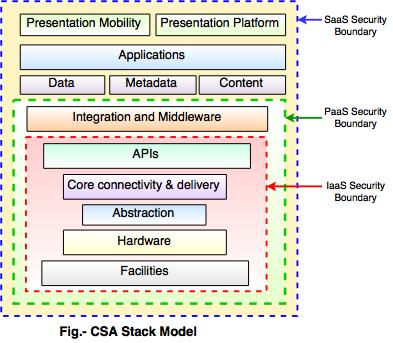
- The boundaries between each service model are defined by Cloud Security Alliance (CSA) stack model.
Following diagram shows the cloud security alliance (CSA) stack model.
 Key things in above model:
Key things in above model:- IaaS is the basic level of service. PaaS and SaaS are next levels of services.
- IaaS gives the infrastructure, PaaS gives platform development environment and SaaS gives operating environment.
- IaaS has the minimum level of integrated functionalities and integrated security while the SaaS has the highest.
- The security boundaries are described in this model. At the security boundary, cloud service provider responsibilities end and the customer's responsibilities start.
- The security mechanism below the security boundary is necessary to construct into the system and should be maintained by the customer.
Data security in cloud
Data security in cloud is an important concern because all the data is transferred using Internet.
Following are the mechanisms for data protection.
I) Access Control
ii) Auditing
iii) Authentication
iv) Authorization
Isolated Access to Data
- Data stored in cloud can be retrieved from anywhere, hence it should have a mechanism to isolate data and protect it from clients direct access.
- To isolate storage in the cloud, Brokered Cloud Storage Access is an approach.
Following two services are generated in this approach:- A broker with complete access to storage, but no access to client.
- A proxy with no access to storage, but access to client and broker both.
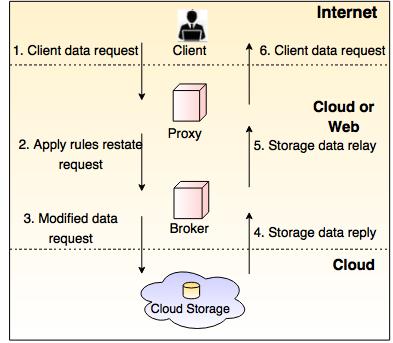
Working of Brokered Cloud Access System
Following are the steps to access the data: - The client data request goes to the external service interface of the proxy.
- The proxy forwards the request to the broker.
- The broker request the data from cloud storage system.
- The cloud storage system returns the data to the broker.
- In next step, broker returns the data to the proxy.
- At the last proxy sends the data to the client.